Sift Security is leveraging big data and advanced analytics to help security teams get more with less. The company recently announced a $3.26 Million funding round. Below is our interview with Neil King, Co-founder & CEO at Sift Security:

Q: What is Sift Security?
A: Sift Security is a next generation platform for security operations. The biggest challenge most organizations face is shortage of qualified security talent. Sift Security was created to help security teams get more with less. Colin Estep, our Chief Security Officer, has Incident Response experience at Netflix, Apple and the FBI. Colin spent a lot of his time proactively hunting for and responding to threats using solutions that didn’t meet his needs. He became frustrated with cumbersome, disjointed solutions that lack intelligence and are challenging to scale. Similar to the experiences we hear from analysts in comparable roles at other large enterprises, Colin was looking for a solution that made his job significantly easier, faster, and more enjoyable. We started Sift Security to create the product that meets the needs of security practitioners like Colin.
 Recommended: Grow Raises $11 Million To Make Its BI Platform Even Faster And Easier To Use
Recommended: Grow Raises $11 Million To Make Its BI Platform Even Faster And Easier To Use
Q: What are your key features?
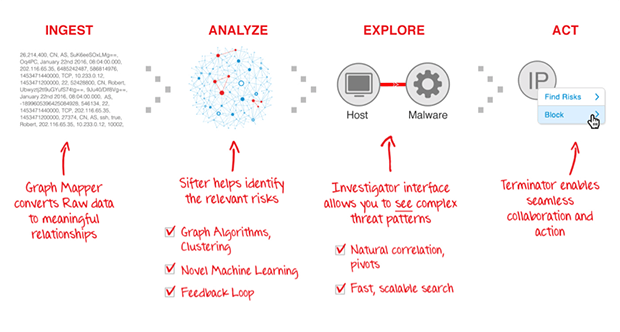
A: Sift Security performs four key functions that align with what we believe are the needs of next generation security operations functions.
Ingest (Graph Mapper) creates a graph data structure and index from raw logs. We focus on existing data (no new agents or network probes) and have out of the box support for data sources such as hosts, network, cloud, application, and threat intelligence. We also offer a self service interface to add custom data.
Analyze (Sifter) combines 3rd party alerts, threat intelligence, rule-based alerts, and advanced machine learning, then prioritizes alerts based on proprietary graph clustering algorithms.
Explore (Investigator) is our UI that centers around a relational graph canvas, complemented by prioritized alerts, scalable search and customizable dashboards.
Act (Terminator) is a workflow and API integration that enables seamless collaboration and action from alert to remediation.
Q: Tell us something more about Sift Security’s Threat Hunting and Incident Response Platform?
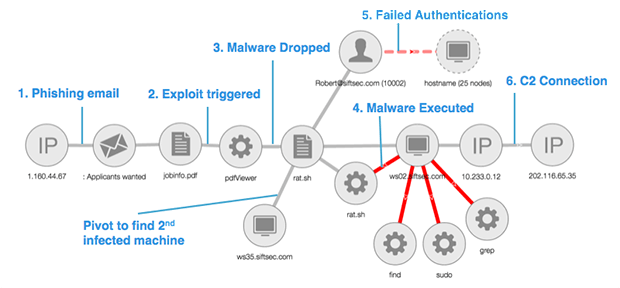
A: While organizations can not prevent every attack, it is imperative to stop adversaries before they achieve their objective, sometime referred to as minimizing attackers “dwell time”. As an example of how Sift Security can help dwell time, consider the above example investigation summary. This investigation started with (6) an alert showing that an internal IP had connected to a IP address known to host Botnet Command and Control infrastructure. Using our graph canvas, the Analyst quickly tied the internal IP address to the associated host, ws02, and noticed that Sift Security’s machine learning algorithms identified (4) anomalous processes that appear to be reconnaissance activity and possible malware. The Analyst then passed the alert to an Incident Responder, who identified the root cause, a (1) Phishing email, and who also identified a 2nd infected machine. As a result, the Incident Responder took the following actions to protect her organization (a) blocked the phishing and C2 IP addresses, (b) remediated the infected hosts, and (c) updated the vulnerable pdfViewer for all the hosts running that software.
 Recommended: Mac Business Solutions – Exceptional Customer Service From Beginning To End
Recommended: Mac Business Solutions – Exceptional Customer Service From Beginning To End
Q: You’ve recently announced a $3.26 in new funding; what’s your next step?
A: We have assembled an outstanding team of security experts, data scientist, and big data engineers and have an impressive list of pilot customers. In terms of future plans, we are looking to selectively add new customers and partners. On the product side, we are listening carefully to our customers and rapidly adding / improving features that make security operations easier and faster. One of the areas we are excited about is the results we are seeing from our machine learning and graph algorithms, and we look forward to sharing those results publicly in the near future.
Q: What makes Sift Security a good choice?
A: Our customers are telling us that they are able to get their jobs done significantly faster without many of the frustrations they previously experienced. For example, Ken Silva, VP Platforms at Ionic Security, reported that “Sift Security reduces time it takes for his team to investigate alerts from days to minutes.” What differentiates Sift Security from tools like Splunk is that we built our software from the ground up to leverage graph data structure. Built upon this foundation, our software delivers the following key benefits (1) economic and technical scalability, (2) natural correlation, (3) advanced analytics, and (4) super simple interface and workflow.
Activate Social Media:


