Coronet enables faster adoption of SaaS and Cloud-based services while offering enterprise-level protection on all major platforms. Coronet aims to secure any SaaS usage and eliminate the security challenges and threats that come with wireless network connectivity. Additionally, their cloud-based security approach is inexpensive requiring no hardware. Below is our interview with Guy Moskowitz, CEO & Co-Founder of Coronet:

Q: What problem is Coronet solving?
A: All enterprises today rely heavily on SaaS and cloud services. It doesn’t matter if it is IT sanctioned or shadow IT, the bottom line is that you can find hundreds of SaaS and cloud-based services at every organization regardless of size.
The problem starts when you want to secure these services. On the one hand, integrating these services into the current security infrastructure is complex, expensive, and requires a long process; too often, unfortunately, this results in degradation of the user experience. On average, it takes between 4-8 months to integrate a single Cloud or SaaS-based service, such as Office 365 or Box. Obviously, this length of time and financial commitment cannot scale for the hundreds of SaaS and cloud services that an enterprise uses daily. The root cause is that legacy security infrastructure was simply not designed to support the fast pace of today’s cloud-based organizations.
Coronet aims to solve exactly this problem: Coronet provides all the security that you need to allow your users to natively use any SaaS or cloud service while eliminating the complex process of integrating SaaS and cloud services into your security infrastructure.
The result is that Coronet enables enterprises to introduce SaaS and cloud services 20X faster, at 10% of the cost, without downgrading the user experience.
 Recommended: DATABASICS Helps Organizations Get Timely, Complete, And Accurate Time And Expense Reports
Recommended: DATABASICS Helps Organizations Get Timely, Complete, And Accurate Time And Expense Reports
Q: Can you explain the function and advantages of Coronet’s enterprise solution?
A: Cloud services are designed with the following key advantages: cost saving, agility and great user experience. Yet by forcing cloud services into an existing legacy security infrastructure, organizations are losing the three aforementioned advantages. Instead what they’ve introduced is more complexity to implement and maintain. Further, the process of introducing new services becomes much slower. Finally, attempting to connect to a cloud service when logging in from a hotel Wi-Fi, via a container or VPN, delivers nothing short of a terrible user experience.
Coronet, offers an alternative solution. Instead of forcing a cloud service into a legacy security infrastructure, Coronet is the first company that enables users to securely use cloud services — natively, meaning: from the device of the user, through any network, to any cloud service.
This means no proxy, no containers, no VPN, and no degradation of user experience.
An organization that would like to achieve this needs to take two simple steps. The first step is to install Coronet’s small-footprint application, which works on any device (managed or BYOD). Next, they just need to activate their Coronet cloud-based account. Immediately the full native cloud chain is secured: from the device posture, the infrastructure the user is connecting through, all the way to the cloud service itself.
The organization can then add or remove any SaaS or cloud service to its sanctioned IT services list, and can be assured that even if an employee uses their own services (i.e.: shadow IT), the organization is still secured. And since Coronet requires no customization or integration into the legacy security systems, this can be done in minutes, and on a daily basis, providing companies with the needed agility – without the heavy testing or maintenance.
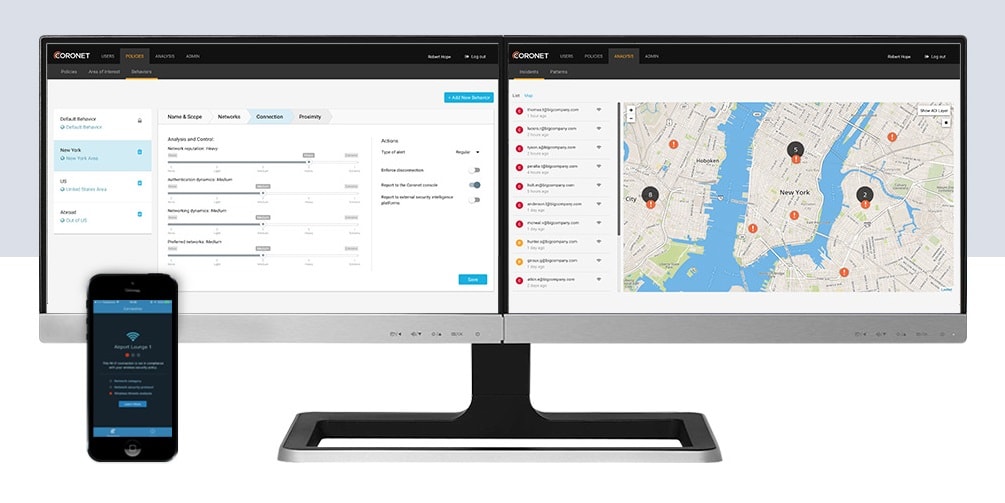
Let’s briefly touch on the nature of cloud security itself. In a legacy security setting, the approach is restrictive. With cloud services, on the other hand, the approach should be how to enable a user to do more, running interference only when there is a real and present danger.
Coronet’s advanced security engine is based on “elastic security.” This is where it is flexible enough to identify the user, how dangerous is the environment, how safe is the connection, how safe are the surroundings as well as many other parameters. This fine granularity of assessing the security situation the user is in is the key to identifying the exact situation and the real danger, and only then to limit the user. We introduced the first version of our technology in our R2 release, which received strong market acceptance followed by industry awards. Since then we’ve improved our solution even more.
Lastly, there is the whole issue of maintenance. One of the major benefits of SaaS services is that they were built to continuously deliver new, enhanced functionality, adjustments and fixes in rapid, ongoing bursts. Users are very happy with this benefit, but for the security team this is actually a nightmare – for each new release. In cases where the service was integrated into the security infrastructure, the security team needs to do verification, customization if needed, and testing of the whole chain. This is deployment requirement so tedious that we often talk to and see some organizations that decided to limit the amount of cloud services or even to just deny any and all service upgrades and enhancements across the board! With Coronet, we solved this problem. By implementing Coronet side-by-side to the legacy infrastructure, with minimal touch points, there is no need to do any customization and regression testing on every SaaS change. In fact, we are doing the testing for the enterprises, so that the companies can now always benefit from the latest releases and native SaaS experience without worrying about the related maintenance side any longer.
Q: Who is Coronet’s ideal customer and why?
A: Since SaaS-based IT is popular at companies of all sizes, Coronet is a new solution and approach that every organization should consider. We recognize though customer feedback that there is no “one size fits all”. While every company would like to enjoy the benefits of Coronet’s platform, smaller companies would prefer a much better out-of-the-box experience, while larger companies would like to have better capabilities in configuring and customizing Coronet to their exact use cases. Therefore, there are two layers of implementation: while out-of-the-box, all that an organization needs to do is install a client and activate a SaaS-based Coronet account. Immediately from here, based on our best practices, the system provides all the security that you need. Concurrently, almost every parameter of Coronet can then be adjusted to the needs of a more complex implementation. Coronet’s platform also provides great flexibility so than an organization can choose to define an unlimited number of use case scenarios and how the system should behave according to each of those cases.
Recommended: Suretly Introduces “Crowdvouching” – Connects Lenders, Borrowers And Vouchers
Q: How widespread is this dilemma whereby employees are bypassing IT and just using cloud services that help them do their job efficiently? What kind of numbers are we really talking about?
A: The numbers around Shadow IT are astonishing. You can find reports by Cisco that claim an average organization has more than 1200 shadow IT services. Meanwhile, another recent use case by another leading vendor found approximately 869 IT services. Regardless of what the exact number may be, it is clear that we are speaking about hundreds of services that the various departments are using in order to accomplish their daily tasks, none of which are not secured or condoned by IT.
Q: What changed in employees behavior that requires a new security model?
A: Here is some information based on our experience while working with the largest organizations: the 3 most popular areas in an enterprise where you can find non-managed cloud services are in IT, Marketing and Sales departments. Another interesting observation is that, in most cases, the more senior a person is, the more likely he or she will use unauthorized cloud services.
The picture is very clear: the more demanding, creative and result-oriented the person is, the more likely he or she will need the most comfortable and efficient tools to do their jobs successfully. Therefore, many researchers conclude that organizations need to find a way to embrace this new worker behavior and not limit or try to block it.
With Coronet, enterprises can really enable anyone to use any SaaS- or cloud-based services without being concerned from a security standpoint.
Q: You’ve recently entered into a Distributor and MSSP agreement with Asgent, could you tell us something more about it?
A: Our agreement with Asgent is the latest addition to our growing list of Tier-1 partners. One of the leading security-focused distributors and MSSPs, Asgent manages long-term relationships with many leading enterprises. As many other security providers, they were challenged with how to enable their customers with a traditional security infrastructure, which was also utilizing an increasing number of SaaS and cloud services. While Asgent was doing many projects that involved integrating cloud services into legacy security infrastructure, they noted that their customers are reluctant to continue to integrate services after they completed only a few of them. The reason behind this is simple: since integrating each service requires a few months of time, it could not scale to include the hundreds of services that the enterprise needed. Further, by the time they integrated a service, the request from users was to enable another one – this was the level of agility that was expected.
With Coronet, they could integrate a whole array of services in no time and at a fraction of the cost and time that it took to integrate one service into the legacy infrastructure.
We plan to continue to add more partners, locally, nationally and internationally who will be able to offer Coronet services to more enterprises worldwide.
 Recommended: ERPLY Delivers Enterprise-Grade Solutions For Small And Medium-Sized Retailers
Recommended: ERPLY Delivers Enterprise-Grade Solutions For Small And Medium-Sized Retailers
Q: On average, how long does it take and how much does it cost a company to integrate a cloud-based service so they have full visibility and full control of it before rolling it out to employees? How long then does it take for Coronet to integrate a cloud service into its platform?
A: Before we get into pricing, it’s important to understand what’s required from an organization that would like to integrate cloud services to its legacy security infrastructure.
Typically, such integration is built from the following:
Planning: since the legacy security infrastructure is an array of integrated elements from various vendors (or as IT calls it, the “spaghetti”), every new service integrated needs to fall into a specific release and version. Typically, in enterprises these releases are done every 5-8 months.
Customization and integration: to integrate the cloud service, there are several touch points. Following are just the three major ones:
-integrating the needed parameters into the Active Directory (or other central database of users in the enterprise)
-integrating the service into the container/VPN chain at the end-point,
-and finally a configuring the exfiltration systems.
Obviously, there are many other touch points, but just taking those two, typically takes a few months. This includes testing the wrappers, making sure all the communication goes through and doesn’t stop the service that it has to operate even in the limited conditions of a container-VPN-exfiltration working properly, on different systems (laptops/desktops/mobile devices) as well as inside and outside the enterprise facilities.
Using middleware such as CASB or Service GW to interface to the cloud service itself: This is the simplest element of the integration, but as the leading analysts recommend, organizations need to assume that they might require several middleware vendors in order to properly implement all the services that they need, and this does not come cheap. Not even hardly.
Looking at the integration process above, the golden numbers are 4-8 months of integration, and between $500K-$1 million per service at a large enterprise. Obviously, this type of price-prohibitive economics cannot scale to support the hundreds of services that any enterprise needs to secure.
With Coronet, however, the golden numbers are that typically, for the time and cost that it will take an organization to integrate a single service to the legacy security infrastructure, all the services that the organization need would be introduced.
Activate Social Media:


