Below is our recent interview with Eric A. Williams, the Founder & CEO at ijura:

Q: Could you provide our readers with a brief introduction to ijura?
A: ijura is a wholly owned startup venture of the global telecommunications giant Tata Communications. I won the company’s annual employee innovation competition. We filed for patents and officially registered ijura as a company in 2018. ijura remains an active part of Tata Communications’ strategic investment to maintain its position as a world-leading digital infrastructure provider.
ijura offers businesses a holistic solution to cybersecurity vulnerabilities leading to corporate data leakage. Our product is a cloud-based platform that protects smartphones, tablets, and IoT devices against real-time cyberattacks without costly overhead or impacting performance.
ijura is not only for the enterprise. Our cloud-based threat defense solution is now available for individual smartphone owners. Equipped with parental controls, the ijura Mobile Threat Defense (MTD) app secures your device against phishing attacks from emails, infected websites, WhatsApp or SMS/text messages. Consumers can download ijura protection for iPhones and iPads at the Apple App Store and for Android devices at Google Play.
 Recommended: Trella Health Delivers Innovative Business Development Solutions for Post-Acute and Acute Care
Recommended: Trella Health Delivers Innovative Business Development Solutions for Post-Acute and Acute Care
Q: Can you give us insights into your cloud-based solution?
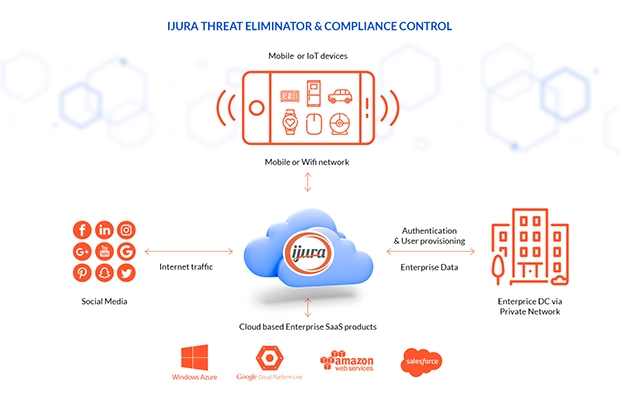
A: ijura is a cloud-based mobile threat technology solution that integrates with your mobile telecommunications operator. You can more easily protect devices and data, including apps and email, while still respecting employee privacy. Our software can recognize and reject suspicious apps, links, messages and sites so employees won’t even have the temptation to click. A cloud solution can be cost effective, simple for employees to adopt (single opt-in, for example), and your network manager or ops person won’t have to rely on your weakest security link — humans — to make critical updates.
ijura fully protects users from malicious content in real-time without any impact on device performance, latency, or battery life — even when accessing streaming data across both public and private environments. And, because the ijura solution doesn’t require any third-party app installations, integrations costs are significantly lower. Enterprise applications can be deployed as easily as consumer ones, increasing speed-to-market through rapid onboarding. Thousands of devices and IoTs can be protected instantly in a truly agnostic way, providing a guarantee of much stronger ongoing security compliance.
Q: What kind of attacks can you detect/prevent?
A: The use of mobile devices in the workplace has exploded. Growing numbers of employees are accessing sensitive corporate content on the same device from which they are checking Facebook, downloading games, and emailing friends. By far the most common way for a device to be attacked is when users download a malicious app or click a malicious link in a phishing email.
ijura blocks malicious data traffic and makes it easy to enforce content access policies across a globally distributed estate of mobile devices and IoT, protecting enterprises and users from malware, spyware, phishing and other types of cyberattacks. Unlike Mobile Device Management (MDM) solutions which merely secure corporate applications and data on an employee’s mobile device, ijura has a zero-trust approach that protects everything, including personal applications and email.
Q: What are the biggest challenges in cybersecurity for mobile devices?
A: Mobile security is at the top of every company’s worry list these days. The mass adoption of workplace BYOD (Bring Your Own Device) has dramatically expanded the threat landscape. No connected device is immune. Increasingly, employees are accessing corporate data from their personal smartphones and tablets, further complicating the Mobile Threat Defense puzzle.
Personal apps can be a serious exposure point, as many hackers use legitimate apps to create trust with users whilst getting them to pass over sensitive information or download malicious content. Yet personal applications and data usually fall outside the remit of corporate device management and security policies, making it nearly impossible to get every employee to make critical security updates.
Traditional anti-virus and anti-malware software may be enough for the corporate network and endpoints, but simply do not provide the holistic protection required for smartphones and IoT devices. A cloud-based solution like ijura, when integrated with a mobile operator, can easily protect all employee devices and data, including apps and email, while still respecting employee privacy.
Q: Why is ijura the clever option when it comes to securing mobile data?
A: With ijura, enterprises can outsmart cybercriminals so well that the criminals won’t even be aware of the protective solution that is thwarting their attack. Unlike competitive solutions that sit on the device, the ijura cloud-based solution is undetectable. Hackers can’t see, access, bypass or shut it down.
The ijura subscription-based commercial model substantially reduces the cost of securing mobile and IoT devices when compared to Mobile Device Management. No need for hardware, hosting or server investments or expensive consultants to implement it. Companies simply pay a one-time charge for integration and set-up and then a fixed monthly subscription.
With ijura, updates happen automatically, meaning no IT time will be spent on patching or upgrading hardware. And because ijura manages all IP access at the enterprise level in the cloud, companies can better control associated costs for data and roaming incurred by their globetrotting employees.
 Recommended: Insurance Brokerage Shirley Invests 10% Of Profits In Women-Led Companies
Recommended: Insurance Brokerage Shirley Invests 10% Of Profits In Women-Led Companies
Q: What are your plans for the future?
A: We’re committed to developing and retaining the very best talent to ensure our ability to offer cutting-edge innovation delivered in a simple, user-friendly way to our customers and their employees. We are looking to invest in Artificial Intelligence (AI) in order to achieve a higher level of modern real-time threat detection capabilities and thwart zero-day attacks with a greater level of confidence.
We are also tapping our relationship with Tata Communications to help customers and partners access a wider set of capabilities to support their business needs and drive the outcomes they require — for example, next-generation intelligent networks, connectivity and IoT services.
Activate Social Media:


