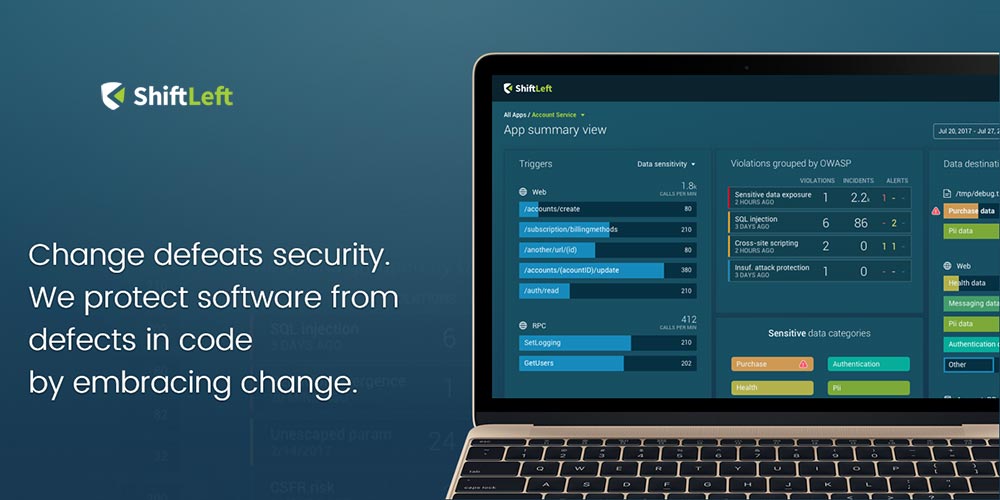
ShiftLeft is the first security solution that brings together two facets of code – source code analysis and runtime behavior of software. This approach of informing the runtime behavior of an application with findings from code analysis makes runtime protection more comprehensive and accurate. The common language called Security DNA allows all three personas – Developers, DevOps, and SecOps – to collaborate and enhance the security posture of the software.
Below is our interview with Manish Gupta, CEO and Co-Founder of ShiftLeft:

Q: Congratulations, I heard ShiftLeft recently launched from stealth mode. Can you tell us about the company?
A: ShiftLeft was founded in late 2016 by Chetan Conikee, Vlad A Ionescu, and myself. Our motivation to start ShiftLeft was to integrate security and compliance into the Continuous Integration/Continuous Deployment (CI/CD) pipeline, thereby bringing the same agility to security that DevOps brought to infrastructure. Let me elaborate. The fundamental problem that ShiftLeft is trying to solve is protection of software that is resident in the cloud and changing at an unprecedented pace. Today companies developing software also host the software for their customers and partners. This gives us an opportunity to protect the software by first understanding the security needs of the code in development. That’s what we do at ShiftLeft. For every version of every application we extract its Security DNA (all security relevant elements in source code) by analyzing the code and creating a custom security agent to protect the specific version of the application.
We are a fast-growing company with a diverse mix of talent from security, cloud infrastructure, big data, and web scale companies. Because the team understands the challenges of developing and securing cloud-native applications, we have a unique advantage of having experienced firsthand the pain point that ShiftLeft solves.
 Recommended: Cloud For Utilities Announces The Inaugural Cloud For Utilities Summit
Recommended: Cloud For Utilities Announces The Inaugural Cloud For Utilities Summit
Q: Can you give us more insights into your solution and what it does that is unique?
A: ShiftLeft is uniquely differentiated in a number of ways. First, we are not focused on threats. ShiftLeft does not rely on checking apps against known security signatures. It identifies vulnerabilities at build-time by analyzing source code or bytecode and uses that knowledge to inform runtime protection.
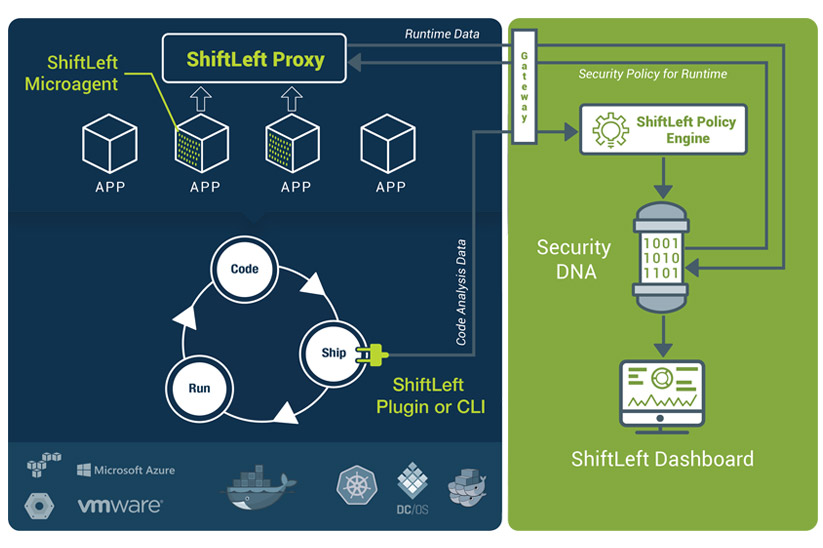
Next, we are all about agility, just like the DevOps and SecDevOps communities we serve. ShiftLeft’s approach leverages agile CI/CD to enhance security. We extract security DNA and create a runtime agent for an app as many times as that app is upgraded. So we embrace change as opposed to being defeated by pace of change, which has been the security industry’s Achilles heel to date. The speed which new threats and malware spread makes it nearly impossible for security products to keep up.
Finally, ShiftLeft, is infrastructure agnostic. It is agnostic to cloud infrastructure, virtual machines, containers, bare metal, etc. ShiftLeft has two integration points in the CI/CD pipeline – build-time, through a plugin or command-line interface for continuous integration tools; and runtime, through an agent that is attached to the application. We do not use any constructs of the infrastructure, so we are widely applicable across all infrastructures.
Q: Why is it so difficult to ensure that applications are secure?
A: The challenges today in making applications secure are two-fold.
First, there is the widespread adoption of cloud. Cloud computing is one of the most disruptive forces of IT with 41 percent of workloads in the public cloud, according to 451 Research. But most security products were developed for the time when enterprise software was shrink-wrapped and deployed in the data center. The prevailing best practice for such an environment was to deploy multiple layers of security in front of the data center – all of which focus on threats (viruses, worms, malware). This approach is ill-suited for cloud-based software, where a company has access to neither the operating system nor to the network of their infrastructure. The only thing that they have access to and own is the application itself. The threat-focused security approach does not cut it for this new world of cloud software.
Then, there is the pace of change. As the pace of software development increases and the use of open source software (OSS) and third party libraries becomes more prevalent, more applications are being assembled as opposed to being developed from scratch. This presents a dual problem for Developers and for DevOps/DevSecOps. The pressure of releasing new features faster does not give developers enough time to either read through the documentation or review the code of the OSS libraries they use. There are also frequent cases of developers accidentally writing sensitive data or credentials to a third party API or sink unencrypted. The sprawl of OSS and third party API or libraries used makes it difficult for DevOps and DevSecOps to patch for known vulnerabilities in OSS.
Securing applications has to match the pace of change of cloud-based software and the level of automation that CI/CD has brought to software development lifecycle. At ShiftLeft, this is the problem we are solving.
Q: Who are your clients and what market are you targeting?
A: Our clients primarily include born-in-the-cloud companies using CI/CD processes and doing frequent releases. Our target markets include technology, banking, and healthcare. We are also working with traditional enterprises which are moving their workloads into the cloud.
 Recommended: Cartika Helps Its Clients Manage Big Data And Meet Compliance Through Its IaaS Cloud Platform
Recommended: Cartika Helps Its Clients Manage Big Data And Meet Compliance Through Its IaaS Cloud Platform
Q: Can you tell us about your direct buy option? Isn’t this pretty unique in the security industry?
A: The traditional go-to-market model for security has been to hire an army of sales and initially focus on fortune-1000. But with the movement of software into the cloud, organizations are already practicing the agile, self-service model. The movement of software into the cloud is shifting software consumption to a SaaS model that is much more nimble and agile. Organizations are also warming up to Try-Buy. Evaluating a solution with a free trial and upgrading to a paid service is the typical buying behavior of the DevOps persona, who is increasingly becoming responsible for the security of cloud software.
ShiftLeft is not only changing how we think about security for cloud-based workloads but also how security products are sold.
Q: What are your plans for the next 12 months?
A: As a startup, our key focus will be on our go-to-market strategy and customers. We have been fortunate to have a Customer Advisory Board from the inception of the company that helped validate our assumptions, prioritize pain points and inform our go-to-market strategy. We will be accelerating our inbound marketing efforts over the next several months in addition to rounding up the product to support more languages.
Q: It has been great speaking with you. Is there anything you would like to add around DevOps or cloud security?
A: Cloud has fueled innovation in unprecedented ways, enabling companies to meet customer requirements faster. But change disrupts security, making it easier for attackers to exploit. The biggest security problem for the next decade is to figure out how to protect cloud software without slowing innovation. At ShiftLeft, our mission is to be the enabler of security for cloud software.
Activate Social Media:


