Every CISO I know has said this line in one form or another – “You should not assume you will not be breached. Instead, you should act like you will be, and prepare accordingly”. Titaniam offers a framework and solution for how to practically implement this advice.
Let is break down what a CISO needs in order act on this advice. Practical action boils down to three things: First, assume that you are truly breached and identify assets that would be disastrous in the hands of attackers. Second, assume that the breach bypasses typical defenses and put a plan in place to protect these assets even when that happens. Third, have a way to monitor the “immunity” of these assets at all times.
 Recommended: Meet Cedalo – Real Time Broker And Spreadsheet For IoT And B2B Stream Processing
Recommended: Meet Cedalo – Real Time Broker And Spreadsheet For IoT And B2B Stream Processing
Do you have this in place?. For most enterprises, this list of top assets includes valuable data. Titaniam offers a leading edge solution to implement this plan for valuable enterprise data.
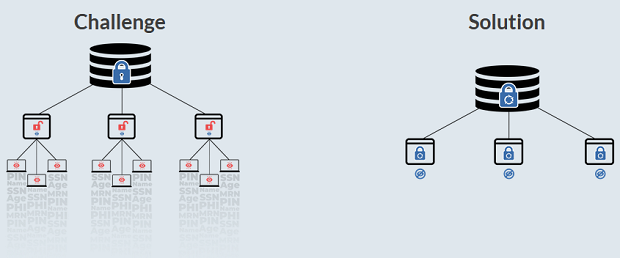
It is now well understood that major compromise of enterprise defenses typically involves significant access compromise. This means attackers gain admin privileges, or root access, or some other way to access and exfiltrate large volumes of valuable data in clear text. How can enterprises make their data immune to this type of breach?
The answer lies in extending the traditional notion of data protection which typically covers encryption for data-at-rest and data-in-transit, to cover data-in-use. Attackers with credentials tend to access data the same way a legitimate user would, and this makes it impossible for regular security controls to detect or prevent the compromises. Titaniam offers data protection that remains present at all times. It does not come off when the data is queried, or indexed, or searched, or analyzed, or being otherwise manipulated in memory. When protection stays on regardless of access privileges, that data becomes “immune”.
Enterprises need this type of immunity to reduce their risk against undetected attackers that stay present in their networks for long periods of time. Enterprises also need this type of immunity to meet data privacy requirements.
 Recommended: Airbyte Has Recently Raised $5.2 Million In Seed Funding
Recommended: Airbyte Has Recently Raised $5.2 Million In Seed Funding
Titaniam offers this capability in a variety of form factors. From platform plug-ins, to API services, to proxies and language libraries. We have all the pieces that enterprises need to construct a system that fits current architecture regardless of whether it is in the cloud, on prem, or a mix. That combined with the portability of this immune data, key management and most importantly, a data immunity dashboard, gives the CISO both visibility as well as control over the protection and privacy of their most important data assets.
2019 was all about beefing up security in the face of alarming data breaches. When the breaches remained relentless despite out increased investment in security, we spent 2020 investing in resilience. Breaches have only become worse. And even though we have learned to recover better than we ever did, the data compromises continue to haunt us. Compromised data becomes the fodder for subsequent breaches and the cycle becomes larger and larger with each iteration. This is why 2021 is going to be the year we talk about immunity. The Data Immunity dashboard from Titaniam is a critical tool for the CISO. And Titaniam’s Adaptive Data Protection Platform, is a must have in the face of the security and privacy challenges of our modern data driven world.
Written by:
Arti Raman
Founder/ CEO Titaniam, Inc.



