* – This article has been archived and is no longer updated by our editorial team –
Below is our recent interview with Doug Dooley, COO at Data Theorem:

Q: Can you provide our readers with a brief introduction to Data Theorem?
A: Yes, I would be happy to. Data Theorem was founded in 2013 by Himanshu Dwivedi, who is 20-plus year veteran in the security industry going back to his days as a security researcher at @stake, being one of the co-founders of iSEC Partners, and an author of six security hacking books. Data Theorem’s mission is to analyze and secure any modern application – anytime and anywhere. Data Theorem’s TrustKit allows companies to build safer apps that protect data better. TrustKit uniquely scans modern applications on a continuous basis in search of security flaws and data privacy gaps. In fact, we recently announced that since TrustKit’s release in 2015, it has identified more than 100 million eavesdropping attempts on iOS and Android applications, where apps in active mode have blocked 100 percent of those attempts.
Q: And can you tell us a little more about TrustKit?
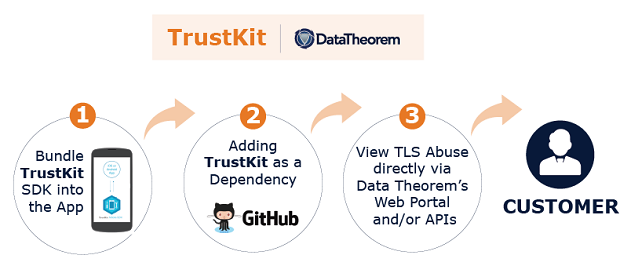
A: TrustKit, with its growing community of thousands of application developers, is furthering anti-eavesdropping as a new standard in mobile application security. It enables a SSL Pinning framework so mobile apps can protect the privacy of their data transmission. While SSL pinning has existed as a concept, the TrustKit free open-source SDK is the industry’s first solution to significantly ease the equipping of mobile applications with SSL pinning, enabling them to encrypt all communication and actively stop eavesdropping and block SSL man-in-the-middle attacks. This helps ensure user privacy, maintain data integrity, stop unauthorized spyware, and block unknown attackers from stealing user identity.
 Recommended: Interview With Matt Choi, Founder And Chief Strategist Of Certus Trading
Recommended: Interview With Matt Choi, Founder And Chief Strategist Of Certus Trading
Q: And what will the new TrustKit Analytics Service you just launched offer?
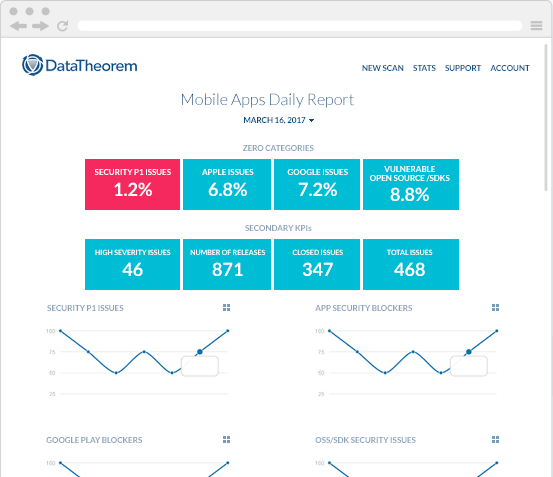
A: TrustKit Analytics is a new and free service for the TrustKit community of developers and security professionals, delivering global visualization (geotagging) of the locations with the most eavesdropping attempts. The analytics service shows what percentage of eavesdropping attempts were actively blocked versus passively monitored, and whether the attempts came from end user device spyware, insecure public Wi-Fi, or corporate employer network monitoring. TrustKit Analytics also provides an easy path for customers to avoid irreversible downtime by setting up alerts to prevent malicious domain forging of SSL certificates and early detection of pinning misconfigurations. These alerts help customers avoid embarrassing mistakes and the loss of business due to avoidable downtime.
Q: Why is now the time for a technology solution like Data Theorem?
A: The rate of modern software development has accelerated to a point where legacy security solutions struggle to keep pace with most DevOps environments. The foundation of Data Theorem’s analyzer technology has been designed with automation and rapid detection with correction of vulnerabilities as core benefits. Data Theorem accelerates and scales software changes, updates, and fixes vulnerabilities by being tightly integrated into customers’ software development lifecycle (SDLC). Some of the common integrations that help customers automate and speed up vulnerability fixes include a wide range of Agile-centric CI/CD build and bug tracking connectors like Jenkins and JIRA. Ultimately, Data Theorem is a platform for modern application security built for speed and growth.
Q: How exactly do you scan and secure mobile apps? Shouldn’t Google/Apple do that?
A: Data Theorem’s cloud-based technology scans iOS and Android apps on a continuous basis in search of security flaws and data privacy gaps. The technology scans apps in public app stores (Apple App Store, Google Play, Windows Mobile, Amazon App Store for Android), internal app stores with in-house or 3rd-party apps, or apps distributed via Air-Watch, MobileIron, Good, etc. For any given issue, Data Theorem provides developers full access to Objective-C, Swift, Java, and C# code that fixes any identified issue. After a scan is completed, the technology provides actual code that will help lock down the high-risk areas of a mobile application. The code is not proof-of-concept, but real code used in high-performance mobile apps. As an example, Data Theorem’s TrustKit secure code library has been downloaded several thousand times with over one million installs, like mentioned earlier.
Apple and Google provide some baseline standards around security and privacy for publishers that wish to submit to their app stores. However, their business models have incentives to ensure the most popular applications regardless of their security quality are always available to their mobile customers. Further, the guidelines from the mobile OS providers continue to change on a periodic basis, yet verifying and enforcing even the most basic security standards would require a massively scalable run-time binary analyzer. Apple and Google are responsible for the core operating system, but they leave the application layer, and its security, to the publisher. Data Theorem has invested significant engineering resources to develop a fast and scalable run-time analyzer that can dynamically assess Android, iOS, and other modern applications. This supports our business model and mission to find security vulnerabilities and remedies that keep our customers’ applications safe and their data protected.
 Recommended: e-Learning Software Easygenerator Allows You To Start Creating Courses Fast
Recommended: e-Learning Software Easygenerator Allows You To Start Creating Courses Fast
Q: If we compare App Store to Google Play Store, which one is more secure? And why?
A: Apple and Google both have positive and negatives in terms of security; however, neither is superior over the other, despite what you read in hyped-up media articles. Overall, Google is an open ecosystem, which gives developers a lot of flexibility, but extra flexibility comes with a larger security attack surface. On the contrary, Apple is a closed ecosystem, where developers do not have a lot of flexibility, which reduces the overall attack surface of the platform. Both operating systems have a sandbox model, which prevents one app from accessing the data and memory from another app, which is very strong; however, each OS is exposed to 3rd-party commercial SDKs and open source libraries, which have full access to an app’s data, network, and private storage. Overall, neither is more secure, but have different exposure levels since the OSes have been architected differently. The problem is not so much the operating system (iOS vs Android), but rather the App Store and Google Play. Both app stores are designed to encourage downloads, which promote features way more than security, especially when it comes to the exposure of end-user data. For example, both the App Store and Google Play allow developers to publish apps with major security issues that allow end-user data to fall in the hands of attackers. If the App Store or Google Play would clamp down on these apps, there would be far fewer downloads from their stores, which almost guarantee both Apple and Google won’t.
Q: What are your plans for the future?
A: Modern applications developed by companies innovating at a rapid pace align best with the future of what Data Theorem is building. Many of these forward-leaning companies have given us a glimpse of what’s ahead in the future. We believe customers over the next 3-5 years will experience significant growth in API-connected microservices in the public cloud. Today, mobile apps consistently connect to more API-driven services built by their own companies and other 3rd parties. The dynamic assembly of data coming from an amalgamation of API services is making applications more valuable and insightful. However, protecting data and assessing risk in this dynamic world of modern software is becoming more challenging than in the past. As a result, expect to see new security services from Data Theorem to help customers in an API-connected world.
Activate Social Media:


