Cyber adAPT’s mission is to protect confidential enterprise digital assets and hard-earned reputations without compromising network performance. Cyber adAPT’s security platform brings 100% of BYO traffic inside the firewall for monitoring. The technology instantly illuminates otherwise hidden threats that made it through perimeter defenses (some reported breaches have gone unnoticed for up to 200 days). Below is our interview with Kirsten Bay, President & CEO, Cyber adAPT:

Q: Kirsten, how would you describe Cyber adAPT in your own words?
A: Cyber adAPT’s vision is to redefine next generation cyber defense. Through years of industry experience and research, our security platform was created on the premise that most enterprise networks have already been breached. This dangerous situation is compounded by the influx of mobile and BYO devices, where massive amounts of data is now traveling between networks around the world.
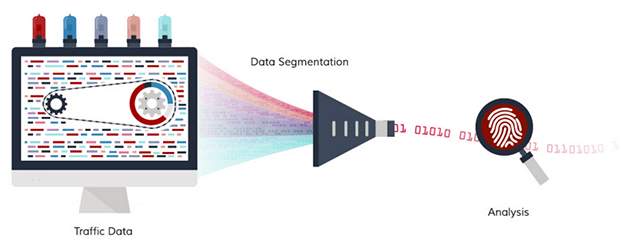
Cyber adAPT’s solution is the only security platform that brings 100% of BYO traffic inside the firewall for monitoring. The technology instantly illuminates otherwise hidden threats that made it through perimeter defenses (some reported breaches have gone unnoticed for up to 200 days). It is our mission at Cyber adAPT to protect confidential enterprise digital assets and hard-earned reputations without compromising network performance. In a world where both the expense and scarcity of quality labor is on the rise, maximizing the effectiveness of oftentimes wasted security-analyst resources is our prime objective.
Recommended: CyberX – Securing The Industrial Internet
Q: You and Mobile Active Defense recently announced a fully integrated product, tell us something more?
A: We are very excited to announce our partnership with Mobile Active Defense (‘M@D’) and the breakthrough mobile security solution our collaboration can provide CISOs and CIOs worldwide. Combining mobile protection with network detection is critical in today’s mobile-centric enterprise environment.
With BYOD-driven network perimeter expansion, not only does the enterprise perimeter become more porous, but the attack surface of each enterprise grows exponentially. It takes one missed compromise to cause irreparable and costly damage to the organization. Exploiting the vulnerabilities of data-in-motion is becoming an increasingly attractive attack method for hackers and other maliciously inclined actors. The partnership between Cyber adAPT and M@D offers dual layer protection for the mobile-enabled enterprise. We monitor all the traffic between networks and devices while deploying a second layer detection capability, to quickly surface attackers who may have made it through perimeter defenses. The entire solution processes in real-time to identify threats immediately with very few false positives.
 Recommended: Dragonfly – Creates Global Partnerships To Help Tackle Cybercrime
Recommended: Dragonfly – Creates Global Partnerships To Help Tackle Cybercrime
Q: Can you give us more insights into your solutions?
A: Our technology provides CIOs and CISOs certainty that threats to their network are not slipping by unnoticed. Cyber adAPT’s unique algorithms are built to anticipate potential attacks, not just rely on historic attack patterns. Additionally, our technology can distinguish credible threats amidst system noise. With nearly zero false alarms, our engineers have ensured that enterprise security analysts are no longer wasting precious time chasing notifications, nor are they belatedly finding a threat that may have been dormant in their network awaiting the opportune moment to strike.
Q: More generally, how do you see the Mobile Protection landscape developing, and where do you place yourself in the industry?
A: We all know that mobile protection is necessary to enterprise organizations today, and yet it will be a linchpin in all security plans as BYO and mobile device usage continues to grow.
Whiles Gartner shows BYO device usage at 40% with projected growth to 80% or higher by 2020, the marketplace is learning that most of the solutions for enterprise mobility management do not provide true protection to their users. Our goal is to empower every security professional with efficient tools to stay ahead of the adversary.
 Recommended: Sqrrl – A Better Approach To Detecting And Investigating Cybersecurity Incidents
Recommended: Sqrrl – A Better Approach To Detecting And Investigating Cybersecurity Incidents
Q: What are your plans for next four months?
A: We are getting considerable market traction by finding attacks within minutes of installation, and are working to continue to enhance our solution to continually find sophisticated attackers. Our strong client relationships have been invaluable for fine-tuning our product, and we will continue to define use cases that enhance the user experience.
Activate Social Media:


