* – This article has been archived and is no longer updated by our editorial team –
Below is our recent interview with Doug Dooley, COO at Data Theorem:

Q: You’ve recently released two new products, can you tell us something about them?
A: Sure thing. On Oct. 25, Data Theorem launched two new API Security solutions that mark industry firsts as far as these kinds of solutions.
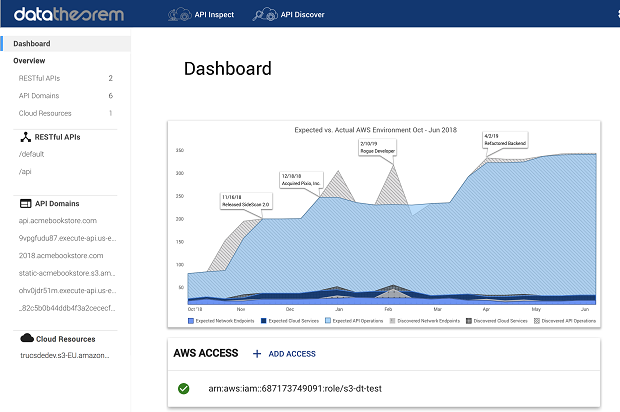
First, we launched API Discover, which works with AWS public cloud accounts today and will work with Google Cloud and Azure in future releases. API Discover continuously finds new APIs and changes to existing APIs created by our customers. Using this, enterprises can now address shadow APIs, which are rogue APIs in use without proper enterprise security vetting that are undetected by today’s legacy security tools.
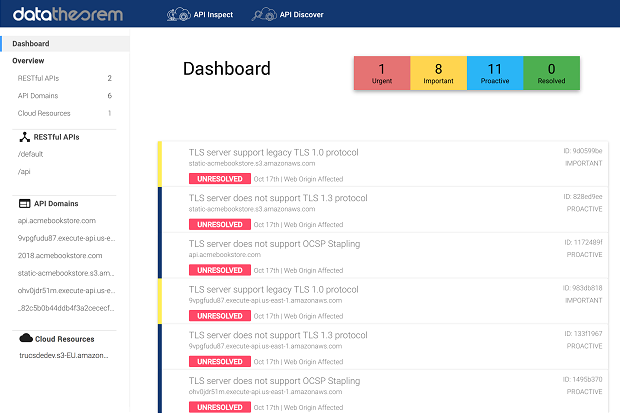
We also launched API Inspect, which continuously and automatically verifies that the operations of APIs always match their intended specs. If any discrepancies are found, a policy-based alert is triggered to notify customers of potential security violations. Depending on the severity of the API issue, a security task will be created to guide customers on how to address the problem.
Q: How are the new solutions your company offers different than traditional application security solutions?
A: For many years coming out of the web services era of SOAP and XML, gateway appliances were the tool of choice to manage API security. These traditional security tools and API gateways were designed to secure against unauthorized access to data residing behind a corporate firewall within the perimeter of an on-premise data center, and are unable to detect today’s newer threats, such as shadow APIs. These undiscovered APIs often run on ephemeral infrastructure in the public cloud, making them hard to find for legacy security tools because modern application frameworks make network-centric gateway tools unusable, non-scalable, or both.
Data Theorem’s unique offering for modern APIs does not use any legacy techniques, such as adding agents or hooks to an operating system (Linux, Windows) or container (Docker). Our offering requires no network choke points like a web application firewall (WAF) or a third party API gateway. Our new API security services are built for modern app architectures and operate well even if the underlying infrastructure is ephemeral, such as serverless (Amazon Lambda, Google Cloud Functions, Azure Functions). Data Theorem has the ability to continuously protect organizations from mistakes made from rapidly changing APIs in production cloud environments – an essential capability for most security and DevOps teams.
 Recommended: Seebo Makes It Easy For Manufacturers To Cut Downtime, Boost Production Yield, And Minimize Product Faults
Recommended: Seebo Makes It Easy For Manufacturers To Cut Downtime, Boost Production Yield, And Minimize Product Faults
Q: Why did you decide to make these new products?
A: After delivering a very successful mobile app security solution for years, which has identified more than 300 million eavesdropping attempts on iOS and Android applications, our teams at Data Theorem saw the need to extend this unique innovation to all modern apps, not just mobile. We could see that today’s agile and serverless application frameworks – such as Amazon Lambda, Google Cloud Functions, and Azure Functions – allow developers to create and deploy modern apps faster and cheaper with less guidance from architects. As great and empowering as this modern app development has become, we saw how it has created significant security issues since it is more difficult to quickly discover APIs being used and continuously analyze their security postures. We made these products because there was a gap in what traditional security solutions could deliver, and what the industry needs around continuous discovery and scanning of all modern enterprise apps.
Q: Could you give us an example of how the new solution works?
A: Yes. Our API Discover solution enables security and operations teams to discover shadow APIs in public cloud environments using our cloud-based Analyzer Engine, which continuously scans serverless applications to find shadow APIs. If a shadow API is discovered, an alert notifies the security teams. API Discover begins tracking the shadow APIs it uncovers, and then engages our API Inspect for analysis. Also, if our platform discovers an API but it does not have a standards-based specification, we will automatically generate a Swagger or OpenAPI 3.0 specification.
API Inspect also leverages our Analyzer Engine, to continuously conduct security assessments on API authentication, encryption, source code, and logging. It ensures the function of APIs matches their respective OpenAPI 3.0 specification. Security teams are alerted about important and critical vulnerabilities caused by insufficient security protections. API Discover and API Inspect work together to deliver visibility into shadow APIs, newly built serverless applications, and ensure that security standards are being met.
Q: How would you describe Data Theorem, Inc. in your own words?
A: Data Theorem is the company that analyzes and secures any modern application – anytime and anywhere. We are uniquely positioned to deliver on this promise through our innovation and expertise in building a highly scalable Analyzer Engine that can handle more than 5 million applications available on Google and Apple App Stores. Further, Data Theorem’s Analyzer Engine was the industry’s only solution that allowed companies to build safer apps that protect data better by applying dynamic run-time analysis on a continuous basis in search of security flaws and data privacy gaps. Also, Data Theorem has given back to the industry by publishing an open-source SDK called TrustKit that was first released in 2015. As of June 28, TrustKit had identified more than 100 million eavesdropping attempts on iOS and Android applications. And when TrustKit active mode is turned on, it blocks 100 percent of those attempts. As of today, TrustKit has identified more than 300 million eavesdropping attempts with its growth continuing to accelerate at a rapid pace.
Activate Social Media:


 Recommended:
Recommended: 