Sift Security’s CloudHunter product is a pioneering detection and response platform focused on securing cloud infrastructure, such as AWS, Azure and Google Cloud. CloudHunter solves the biggest challenges organizations face when securing their public cloud infrastructure: visibility, misconfigurations, threat detection, and incident response. With CloudHunter, Security, Cloud, and Development Operations teams, along with Incident Responders can more easily monitor and protect against risks in their public cloud environment.
Below is our intervew with Neil King, the Founder & CEO at Sift Security:

Q: What are the top cloud security threats for 2018?
A: In 2017, the most commonly reported threat related to cloud infrastructure was organizations mis-configuring S3 buckets resulting in the exposure of sensitive data. CSPs and security vendors like us have added protections to help quickly detect and prevent these inadvertent data exposures which should help alleviate this issue going forward.
Looking forward into 2018, we are hearing from our customers increasing concern about more advanced threats such as compromising a user’s credentials, escalating privileges, and then taking malicious action such as exfiltrating data or mining crypto-currency. Cloud infrastructure is increasing of interest to attackers due to a combination of factors: (a) companies are increasingly shifting higher value workloads to the cloud, which make for attractive targets, (b) compromised cloud resources can be misused to generate profit through bitcoin mining or launching DoS attacks. (c) due to priorities and/or lack of expertise, organizations are often exposing a significant attack surface for bad actors to exploit.
To help us better identify these advanced threats, we developed and recently published an attack chain framework tailored to threats to cloud infrastructure (see Cloud Attack Chain).
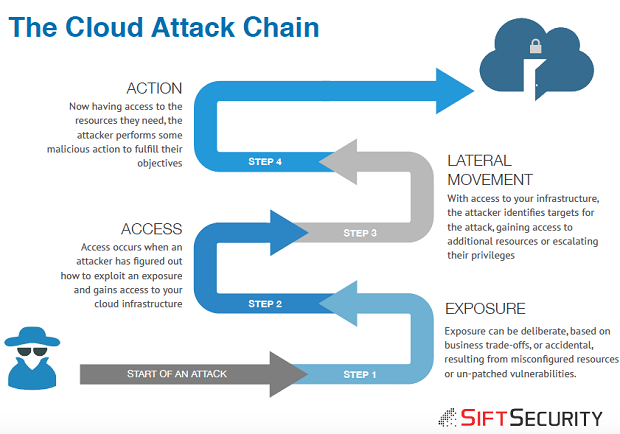
The Cloud Attack Chain is a simplified attack chain model that describes typical attacks on public cloud infrastructure. The attack chain describes how an attacker gains access to a victim’s cloud environment, how they move laterally through the target cloud infrastructure, and what malicious actions they perform. Our new Whitepaper describes the four stages of the attack chain and provides detailed examples of some real-world attacks.
 Recommended: Success Co. Delivers New VR Experience And Learning Tool To The World Of Sports
Recommended: Success Co. Delivers New VR Experience And Learning Tool To The World Of Sports
As a preview, the stages of the Cloud Attack Chain are:
1. Exposure: Exposure of cloud resources is at the beginning of any cloud attack. Exposure can be deliberate, based on business trade-offs, or accidental, resulting from misconfigured resources or unpatched vulnerabilities. This is where attackers start looking for a way in.
2. Access: Access occurs when an attacker has figured out how to exploit an exposure and gains access to your cloud infrastructure.
3. Lateral Movement: With access to your infrastructure, the attacker identifies targets for the attack, gaining access to additional resources or escalating their privileges.
4. Actions: Now having access to the resources they need, the attacker performs some malicious action to fulfill their objectives.
For more on expected IaaS threats, we recently published an overview of cloud security detection use cases which you can see here Public Cloud Detection Use Cases.
Q: How exactly does CloudHunter work?
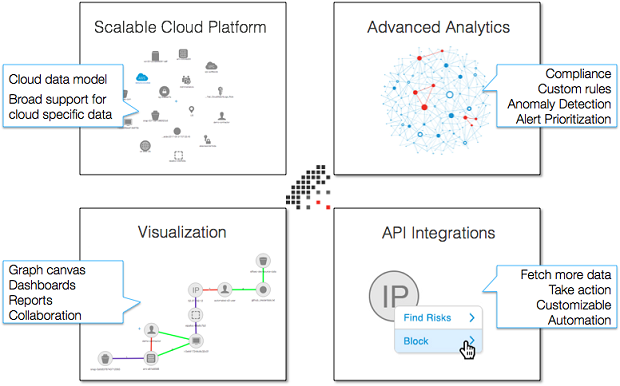
A: CloudHunter has four key components, that work together to help organizations protect their cloud infrastructure:
 Recommended: SimpleCommands Provides Apple Watch Series 3 Users An Easy Way To Access And Manage Their Digital Life
Recommended: SimpleCommands Provides Apple Watch Series 3 Users An Easy Way To Access And Manage Their Digital Life
Scalable Cloud Platform. CloudHunter is built on top of scalable, big data architecture centered around graph database technology. Our team of cloud experts have curated the most interesting data from the hundreds of fields in your cloud logs and APIs. Our data models can provide comprehensive visibility into your cloud infrastructure, including APIs, network, hosts and more.
Security Analytics. CloudHunter combines 3rd party alerts, our own proprietary detections, and highly customizable detections. CloudHunter detection capabilities include: simple rules, correlation rules, anomaly detection, machine learning, and graph clustering algorithms. Together this suite of analytics detects simple compliance and configuration risks; advanced multi-stage attacks; and anomalous, risky behavior. The highest priority alerts & attack chains are surfaced as incidents, which are risks that should be immediately investigated.
Visualization. CloudHunder provides a number of powerful visualization tools to help organizations obtain the required visibility into their cloud infrastructure. One of the most tangible benefits of our graph database is the ability to visually explore your data in the graph canvas. To simplify alert and incident management, we have robust visualization of threats as well. Also, we offer a library of out of the box dashboards, and the ability for users to easily create their own visualizations and dashboards. Finally, it is easy to schedule reports at regular intervals.
API Integrations & Automation. CloudHunter comes with a library of API integrations that enable capabilities like fetching more data or taking action on an entity such as a user or an instance. CloudHunter users can easily add additional integrations to support required use cases for their organization. These integrations can be triggered manually from the user interface, or automatically when rules are triggered, both of which are easily customizable.
Q: You’ve developed a next generation machine learning platform for detecting threats in AWS; can you give us more insights into your technology?
A: All of our detection capabilities start with our security experts defining the threat scenario (use cases). We then determine how best to detect this scenario while minimizing false positives, leveraging one or more of the following capabilities: rules engine, anomaly detection, machine learning, and graph clustering algorithms. Finally, we work hard to make sure our detections can easily be interpreted and investigated, and that they are customizable by the end users of our product. As an example, we might identify a cluster of alerts including (a) anomalous access behavior (b) for a user that is not utilizing MFA, (c) followed by this user anomalously spinning up a cluster of GPU instances (possible bitcoin mining).
Q: You recently announced a new capability to automate typical Incident Response workflows relate to cloud infrastructure; can you share some typical use cases?
A: One of the features our customers appreciate is the ability to seamlessly take manual action directly from our product. For example, if a security analyst identifies an instance that appears to be compromised, they can simply right click on the instance and take a snapshot for forensic purposes (without having to login to the AWS console and figure out how to do that). Many customers have asked to enable these workflows to be triggered automatically, and we released this capability this month (January 2018). Users can now select any of the existing rules, and trigger actions, or create new rules that only trigger actions. Users can choose from a library of predefined actions that Sift provides, or create their own integrations to create their own playbooks.
Activate Social Media:


